
|
|
MULTIPLE SSH REVERSE TUNNELSMultiple SSH Reverse Tunnels
10 SSH Reverse TunnelsThe above example can easily (and very quickly) be extended to use many more tunnels thanks to Docker. Here is the above modified to use 10 tunnels (i.e. n = 11):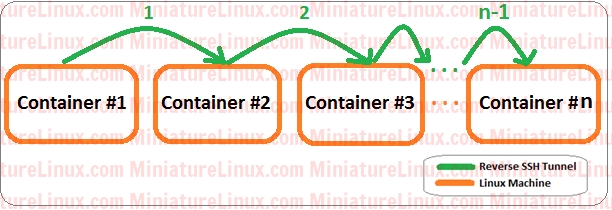 Clean up: docker stop $(docker ps -a -q) && docker rm $(docker ps -a -q) Terminal Tab #1[uses Host Machine's Port 1222) docker run -p 1222:22 -it miniaturelinux/ubuntu-ssh service ssh start ssh -v -R 3333:localhost:22 192.168.10.10 -p 2222 Terminal Tab #2[uses Host Machine's Port 2222) docker run -p 2222:22 -it miniaturelinux/ubuntu-ssh service ssh start ssh -v -R 3333:localhost:3333 192.168.10.10 -p 3222 Terminal Tab #3[uses Host Machine's Port 3222) docker run -p 3222:22 -it miniaturelinux/ubuntu-ssh service ssh start ssh -v -R 3333:localhost:3333 192.168.10.10 -p 4222 Terminal Tab #4[uses Host Machine's Port 4222) docker run -p 4222:22 -it miniaturelinux/ubuntu-ssh service ssh start ssh -v -R 3333:localhost:3333 192.168.10.10 -p 5222 Terminal Tab #5[uses Host Machine's Port 5222) docker run -p 5222:22 -it miniaturelinux/ubuntu-ssh service ssh start ssh -v -R 3333:localhost:3333 192.168.10.10 -p 6222 Terminal Tab #6[uses Host Machine's Port 6222) docker run -p 6222:22 -it miniaturelinux/ubuntu-ssh service ssh start ssh -v -R 3333:localhost:3333 192.168.10.10 -p 7222 Terminal Tab #7[uses Host Machine's Port 7222) docker run -p 7222:22 -it miniaturelinux/ubuntu-ssh service ssh start ssh -v -R 3333:localhost:3333 192.168.10.10 -p 8222 Terminal Tab #8[uses Host Machine's Port 8222) docker run -p 8222:22 -it miniaturelinux/ubuntu-ssh service ssh start ssh -v -R 3333:localhost:3333 192.168.10.10 -p 9222 Terminal Tab #9[uses Host Machine's Port 9222) docker run -p 9222:22 -it miniaturelinux/ubuntu-ssh service ssh start ssh -v -R 3333:localhost:3333 192.168.10.10 -p 10222 Terminal Tab #10[uses Host Machine's Port 10222) docker run -p 10222:22 -it miniaturelinux/ubuntu-ssh service ssh start ssh -v -R 3333:localhost:3333 192.168.10.10 -p 11222 Terminal Tab #11[uses Host Machine's Port 11222) docker run -p 11222:22 -it miniaturelinux/ubuntu-ssh service ssh start ssh localhost -p 3333 Also I should mention that on your Host Machine, you can view the open ports being used by these Docker Containers via typeing: netstat –ntlp
For a more robust production like scenario you would want to use something like -nNTf e.g. like this (i.e. no verbose output etc)
ssh -nNTf -R 3333:localhost:3333 192.168.10.10 -p 3222 Where: -n: Redirects stdin from /dev/null (actually, prevents reading from stdin). This must be used when ssh is run in the background. -N This is useful for just forwarding ports (protocol version 2 only). -T Disable pseudo-tty allocation. -v Verbose mode. Causes ssh to output debugging messages about its progress. |
|
Linux Examples - Comments |
||